In this blog post, we’ll explore how to reverse an array using an 8086 assembly language program. We will walk through the logic, the step-by-step execution, and provide a working code snippet to illustrate the process.
Overall Process:
- The program initializes registers and sets up pointers to the source (
ARR) and destination (REV_ARR) arrays. - It processes each element of the original array, copying it in reverse order to the destination array.
- After processing all elements, the program terminates, leaving the reversed array in memory.
8086 Assembly Code:
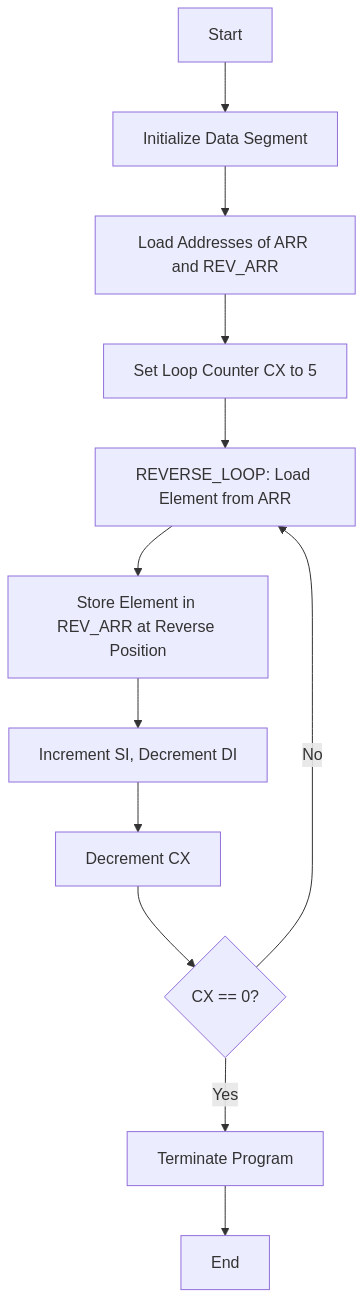
DATA SEGMENT STR1 DB 01H,02H,05H,03H,04H STR2 DB 5 DUP(?) DATA ENDS CODE SEGMENT ASSUME CS:CODE, DS:DATA START: MOV AX, DATA MOV DS, AX LEA SI, STR1 LEA DI, STR2+4 MOV CX, 05H BACK: CLD MOV AL, [SI] MOV [DI], AL INC SI DEC DI DEC CX JNZ BACK INT 3 CODE ENDS END START
Step-by-Step Explanation:
1. Data Segment:
ARR: Defines an array containing the elements{01H, 02H, 05H, 03H, 04H}.REV_ARR: Reserves space for 5 elements to store the reversed array.
2. Code Segment:
Initialization:
MOV AX, DATA: Loads the address of the data segment into AX.MOV DS, AX: Sets DS to point to the data segment, allowing access to variables.LEA SI, ARR: Loads the address of the original array (ARR) into SI.LEA DI, REV_ARR+4: Loads the address of the last element ofREV_ARRinto DI.MOV CX, 05H: Sets the loop counter CX to 5, corresponding to the number of elements.
Loop to Reverse the Array:
REVERSE_LOOP:Label marking the start of the loop.CLD: Clears the direction flag to ensure forward movement.MOV AL, [SI]: Loads the current element fromARRinto AL.MOV [DI], AL: Stores the value from AL intoREV_ARRat the current DI position.INC SI: Moves SI to the next element inARR.DEC DI: Moves DI to the previous position inREV_ARR.DEC CX: Decrements the loop counter.JNZ REVERSE_LOOP: If CX is not zero, repeat the loop.
Program Termination:
INT 3: Generates an interrupt 3, which typically halts execution.
Flowchart
Output
C:\TASM>masm rev.asm
Microsoft (R) Macro Assembler Version 5.00
Copyright (C) Microsoft Corp 1981-1985, 1987. All rights reserved.
Object filename [rev.OBJ]:
Source listing [NUL.LST]:
Cross-reference [NUL.CRF]:
50344 + 450312 Bytes symbol space free
0 Warning Errors
0 Severe Errors
C:\TASM>link rev.obj
Microsoft (R) Overlay Linker Version 3.60
Copyright (C) Microsoft Corp 1983-1987. All rights reserved.
Run File [REV.EXE]:
List File [NUL.MAP]:
Libraries [.LIB]:
LINK : warning L4021: no stack segment
C:\TASM>debug rev.exe
-G
AX=0B04 BX=0000 CX=0000 DX=0000 SP=0000 BP=0000 SI=0005 DI=0004
DS=0B97 ES=0B87 SS=0B97 CS=0B98 IP=001A NV UP EI PL ZR NA PE NC
0B98:001A CC INT 3
-D 0B97:0000
0B97:0000 01 02 05 03 04 04 03 05-02 01 00 00 00 00 00 00 ................
0B97:0010 B8 97 0B 8E D8 8D 36 00-00 8D 3E 09 00 B9 05 00 ......6...>.....
0B97:0020 FC 8A 04 88 05 46 4F 49-75 F6 CC 2A E4 50 B8 FD .....FOIu..*.P..
0B97:0030 05 50 FF 36 24 21 E8 77-63 83 C4 06 FF 36 24 21 .P.6$!.wc....6$!
0B97:0040 B8 0A 00 50 E8 47 5E 83-C4 04 5E 8B E5 5D C3 90 ...P.G^...^..]..
0B97:0050 55 8B EC 81 EC 84 00 C4-5E 04 26 80 7F 0A 00 74 U.......^.&....t
0B97:0060 3E 8B 46 08 8B 56 0A 89-46 FC 89 56 FE C4 5E FC >.F..V..F..V..^.
0B97:0070 26 8A 47 0C 2A E4 40 50-8B C3 05 0C 00 52 50 E8 &.G.*[email protected].
-Q
Understanding the Memory Dump
The memory dump displayed in the DEBUG session shows the contents of memory after running the program. Let’s analyze the key parts:
| Memory Address | Value (Hex) | Explanation |
|---|---|---|
| 0B97:0000 to 0B97:0004 | 01 02 05 03 04 | The input array {01H, 02H, 05H, 03H, 04H} stored in memory |
| 0B97:0005 to 0B97:0008 | 04 03 05 02 01 | The reversed array stored in memory |
This simple yet effective approach ensures that an array is reversed efficiently using assembly language instructions in the 8086 microprocessor.

Can Someone explain this code